The following tutorial assumes the reader is familiar with the following technologies/concepts:
This post is a how to setup Thinktecture’s StarterSTS Identity Server [B1].
1. Download the Source Code from the Codeplex site [at the time of this writing, the current version is B1 Refresh] and unzip it on your local drive.

2) Once the Solution is opened in Visual Studio, inside of the Tools solution folder you will find a Setup project. Run the project by right clicking on it, Selecting Debug –> Start new instance.

3) Set the Location of the Configuration Database as shown below.

You can find the file called IdentityServerConfiguration.sdf inside of the App_Data folder of the Website Project.

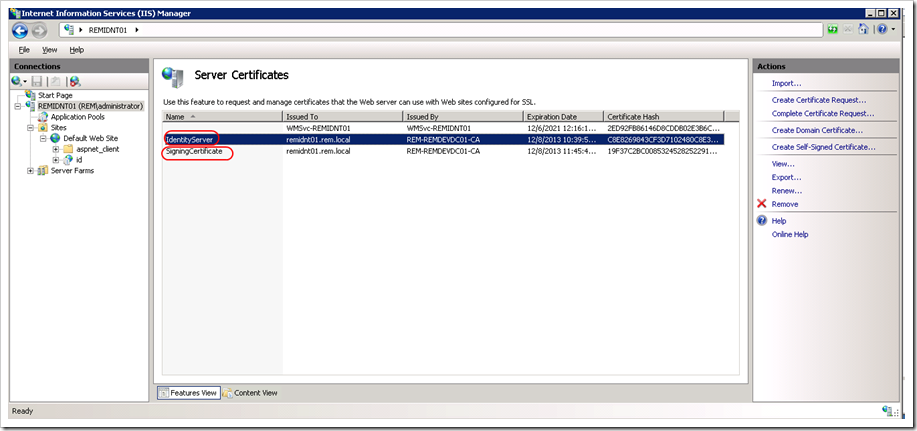
4) Select the certificate that will be used for SSL Encryption. **Note: If you already have IIS setup with SSL, you most definitely want to use the same certificate. I suspect you will, because if you are installing this Identity Server you must be very familiar with the Windows Identity Foundation configuration dance.

5) Select the certificate that will be used for Signing (You can use the same certificate)


After this is done, you might be thinking that you can run the [website] project now and it should just work, right? Thought WRONG! There is no free meal in this world. Our friend Dominick [Baier] has had this running on his machine for a while, so perhaps forgot about setting up IIS, the ASP.NET provider Database and all that business.
SEtting up ThE WEBSITE PROJECT TO USE IIS
So, right after you download the source code, the Web Project Properties looks like so:

Notice the “[X] Use Custom Web Server” option is selected, and points to https://roadie/idsrv/. You want to change these setting as follows:
Switch the setting to Use Local IIS Web Server and enter a more appropriate URL (i.e.:http://[your machine’s fully qualified name]/idsrv), or if you are one cool cat, you may choose Use IIS Express (but then, you are on your own).
We are almost there, do not despair.
CONFIGURING THE ASP.NET MEMBERSHIP DB.
If you were to try to run the Website, you should get this “Yellow page of death”. And that is due to the fact (if you are one of those who do no read error pages) that the 1) you have not installed the standard ASP.NET Membership schema, and 2) the Identity under which IIS is running does not have access to said database (provided it existed). Follow these instructions to setup the ASP.NET application services schema.

After having installed the ASP.NET Schema on your SQL Server instance, go to SQL Server Management Studio, and under Security –> Logins, and make sure that the Identity under which your IIS Application Pool is running has a valid login in SQL Server and has the right access to the ASP.NET database. In my case, the App pool Identity is 'IIS APPPOOL\DefaultAppPool' and the database named "aspnetdb".

Lastly, change the Website\Configuration\connectionStrings.config file to point to your ASP.NET application services database.
<connectionStrings>
<add name="ProviderDB"
connectionString="data source=.\sqlexpress;Integrated Security=SSPI;Initial Catalog=aspnetdb"
providerName="System.Data.SqlClient" />
<add name="IdentityServerConfigurationEntities"
connectionString="metadata=res://Thinktecture.IdentityServer.Core/Repositories.SqlCompact.IdentityServerConfiguration.csdl|res://Thinktecture.IdentityServer.Core/Repositories.SqlCompact.IdentityServerConfiguration.ssdl|res://Thinktecture.IdentityServer.Core/Repositories.SqlCompact.IdentityServerConfiguration.msl;provider=System.Data.SqlServerCe.4.0;provider connection string="Data Source=|DataDirectory|\IdentityServerConfiguration.sdf""
providerName="System.Data.EntityClient" />
</connectionStrings>
If you did everything right, you should now be able to run the application and get this page.

Accessing the Administration Mode of Identity Server
Out of the box, IdentityServer is configured to use the SqlMembershipProvider membership provider implementation. Therefore to login you have to:
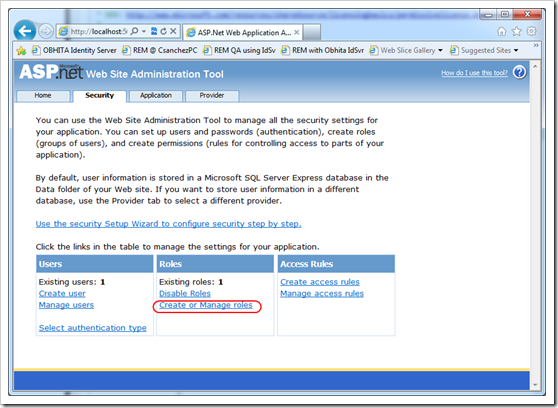
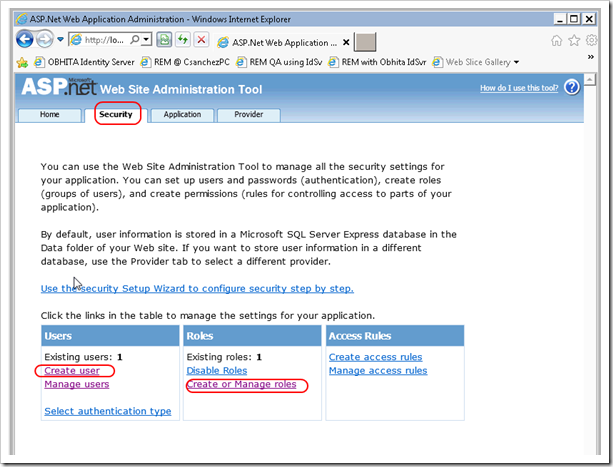
- create a user (i.e.: Administrator)
- create a role called IdentityServerAdministrators.
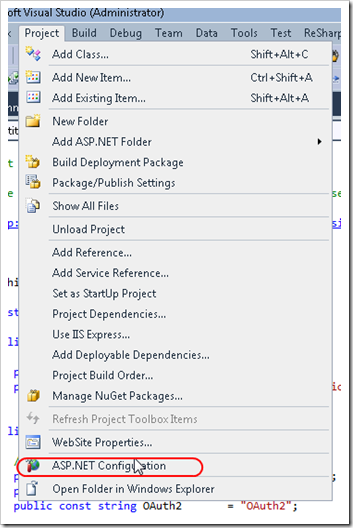
Both of these can be accomplished by using the built-in Web Site Administration Tool (in Visual Studio, go to Project –> ASP.NET Configuration).
[FYI] Contrary to what Dominik Baier’s introductory video says [9:02] , the role the code is expecting is not “TokenServiceAdministrators”, but instead, IdentityServerAdministrators).
[Change for Improvement] This can be improved in the future by modifying the provided implementation of ClaimsAuthorizationManager, and changing the AuthorizeAdministration Method (inside of Thinktecture.IdentityServer.Web.Security.AuthorizationManager)
protected virtual bool AuthorizeAdministration(Collection<Claim> resource, IClaimsIdentity id)
{
return (id.ClaimExists(ClaimTypes.Role, Constants.Roles.IdentityServerAdministrators));
}
The next article will describe how to create a configure your application (Relaying Party) to trust Identity Server as an Secure Token Service (STS).